IT security solutions
Firewalls or intrusion detection systems alone are no longer enough to counter security threats today. Routes of attack are constantly changing – an intelligent, learning security system, awareness, and IT Security Toolbox are the answer.
Tailored to your individual company requirements, single elements of our security solutions can be seamlessly integrated into your corporate processes on a modular basis. We work together here with market leaders like Splunk, Tanium and Crowdstrike.
Solutions
-
Endpoint Security / EDR - XDR
Centralised IT security for all endpoints in the company
Endpoint Detection and Response / EDR - XDR -
Endpoint Security / Endpoint Management
Policy-based end device security management
Endpoint Management
Security Operation Center (SOC)
At the core of an SOC are an >SIEM (Security Information und Event Management) and a >Risk Management Tool. By connecting these two solutions, your company is secured against both internal and external attacks.
We advise you on the integration of existing systems and processes. A needs-based design for your company enables us to keep track of costs and benefits for the launch and >operation of an SOC.
Security Information and Event Management (SIEM)
An SIEM is the central element of a precise security architecture. It unites two essential aspects of data security: security information management and event management.
That’s why good SIEM solutions not only concentrate on managing log data, but can also gather, index, and analyze event data in real time. This makes forecasts on future incidents possible so that data loss or failures don’t even occur.
The German Federal Office for Information Security (BSI) therefore expressly recommends, in particular, that KRITIS companies set up an attack detection system that continuously performs automated recording and evaluation of ongoing operations in its orientation guide for the implementation of attack detection systems.
Consist uses the market-leading SIEM solution Splunk. For the tenth year in a row, the renowned market research institute >Gartner Inc. has attributed this security platform with particularly good solution competence.
Our highly qualified certified specialists advise you on designing the SIEM to suit your company and perform the implementation.
Solution: >Splunk, >Splunk Enterprise Security
We are happy to support you with the maintenance and upkeep of the SIEM through seamless transition to our managed services. Select a select a service package that suits your company or take the strain off your IT department entirely.
Excellent SIEM
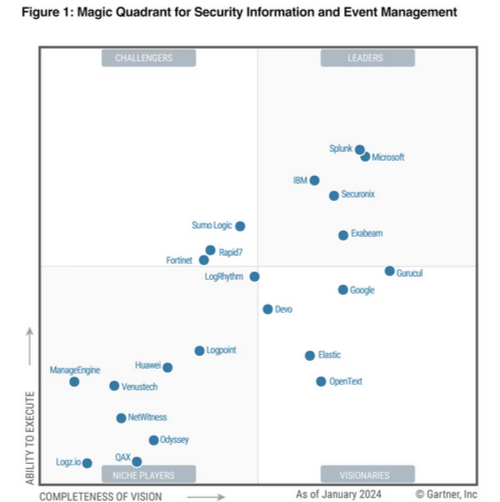
Gartner once again rated Splunk as a market leader in the
> Gartner® Magic Quadrant (MQ) for Security Information und Event Management (SIEM) in 2024.
Security Orchestration, Automation and Response (SOAR)
Once a company reaches a certain size, it makes sense to increase automation of security incident processing. Aside from the fact that analysts are significantly unburdened of recurring tasks, this increases response times to events many times over.
The SOAR platform combines security infrastructure orchestration, playbook automation, and case management functions in order to more effectively link IT teams, processes and tools with one another. This can drastically scale security incidents.
Solution: >Splunk Phantom
Endpoint Security
Endpoint Detection and Response - EDR - XDR
Endpoint Detection and Response (EDR) provides ideal protection for endpoints. They monitor all activities on end devices, analyse them and trigger alarms in the event of suspicious actions.
Extended Endpoint Detection and Response (XDR) is based on the classic EDR approach, but goes one step further and includes not only end devices such as laptops, desktops or servers in the monitoring, but also network, cloud and email security. This makes it better suited to the increasing complexity of IT infrastructures and is also very scalable for both smaller and larger companies.
Even sophisticated threats can be detected and automated responses can be initiated from a centralised console.
Consist uses the market-leading solution > Crowdstrike for this purpose.
Endpoint Management
Efficient endpoint management with the necessary security measures can only be carried out if there is a view of all assets in the company. Tanium enables continuous asset and patch management of all endpoints in the company. Consist is the first accredited Managed Security Service Provider for Tanium in the DACH region.
Solution: > Tanium
E-Mail Security
Individual solutions no longer do justice to the complexity of today's e-mail attacks. With its technology partner Proofpoint, Consist implements a holistic, user-centered response to tactics and gateways of attack vector number 1.
Solution: >Proofpoint
User Behavior Analytics (UBA) - Insider Threat Management
The biggest cyber security threat companies are facing today is no longer a malicious outside attacker. It’s insiders – employees or external service providers with access to company data. With UBA, suspicious and unusual user behavior can be identified for further analysis. What user behavior management does is to separate their normal activities in the company from irregular activities.
For larger companies, it makes sense to employ machine learning algorithms. They provide reliable results with risk analyses and relevant evidence that complements and accelerates the conventional approaches by analysts in Security Operations Centers (SOC).
Our specialists implement and maintain the right solution for your company.
Solution: >Splunk UBA, >ObserveIT|Proofpoint ITM, >Ekran System
Data Loss Prevention (DLP)
Faced with the growing complexity of insider threats, it’s not enough to concentrate solely on protecting data on machines and networks. It is becoming ever more important to incorporate endpoint management through monitoring tools, which protects even privileged users against operating errors and improper behavior. Thanks to pseudonymized data analyses, employee rights and current legal requirements can be taken into account. Compliance requirements should be handled with traceable inspection paths.
In view of the exponential growth of unstructured and semi-structured data, companies often struggle with data-heavy DLP agents at the endpoint, a time-consuming data classification process, ongoing maintenance, and the disruption of the connection between data owners and DLP administrators.
As such, modern DLP approaches are needed which work in harmony with employee rights while staying comprehensive and keeping data levels low. With ObserveIT|Proofpoint ITM, Consist uses a solution that detects insider threats, rationalizes the investigation process, and implements flexible prevention measures.
Solution: >ObserveIT|Proofpoint ITM
Security Awareness
Over 80% of all cyber security incidents occur as a result of human error. Companies lose millions in recovering incidents caused by employees. Classic training programs are often unable to convey the required changes in behavior to employees and provide the necessary motivation. With Proofpoint Security Awareness Training (PSAT) we offer a modern and up-to-date way of training employees at all levels of the company.
Solution: >Proofpoint PSAT
The key essentials for your IT security
- COMPREHENSIVE: Regardless of whether it’s for networks, servers or users, a security solution should possess all the right functions.
- SIMPLE TO MANAGE: All steps should provide simple handling and documentation.
- TEAM-COMPATIBLE: Compatibility with a wide range of data resources and operators is what enables an effective security level.
Your contact

Joscha Sternadel
Portfolio Manager
phone: +49 431 3993-775
mobile: +49 162 2130358
e-mail: sternadel@consist.de

